Data Privacy and Security in PRM Systems

According to the HIMSS Cybersecurity Survey, 95% of healthcare organizations faced a cyberattack last year. Is your PRM system prepared for the next one?
HIMSS Cybersecurity Survey
1. Introduction
According to the HIMSS Cybersecurity Survey, 95% of healthcare organizations faced a cyberattack last year. Is your PRM system prepared for the next one?
Trust is the foundation of healthcare. Patient Relationship Management (PRM) systems build the core of storing all confidential patient data. This makes them attractive to cybercriminals and a key worry for industry professionals. As healthcare professionals, safeguarding this information goes beyond compliance — it’s about showing respect to patients and gaining their confidence.
This article will explain data privacy and security in PRM systems in simple language, cutting through all the jargon. We’ll also look at the laws that shield patient information, concrete ways to secure data, and advice on getting your hands on the most protected PRM system.
Let’s go.
2. The Importance of Data Privacy and Security in PRM Systems
Again, in healthcare, trust is everything. Patients give their most private details expecting it to be kept confidential. So, when healthcare providers fail to protect this data, the trust is broken, and the consequences can be ugly.
Protecting your patients’ privacy isn’t just a matter of good practice; it’s the law. In fact, there are different rules for different countries to safeguard protected health information (PHI). To quickly name a few, HIPAA in the US, PIPEDA in Canada, GDPR in the European Union, and so on. If healthcare systems fail to comply, they are highly likely to face big fines, legal trouble, and long-lasting harm to their name.
Besides the quick costs of looking into the leak and notifying the affected people, there are future problems that can hurt a healthcare group. Once trust breaks, it’s hard to fix. Word about a leak spreads fast, causing loss of existing patients, less money coming in, and a bad reputation that might take forever to improve.
On top of that, stolen patient information significantly increases the chances of identity theft, insurance scams, and other harmful actions. This makes the damage even worse.

3. Regulatory Requirements for PRM Systems
HIPAA: US Health Data Privacy
The Health Insurance Portability and Accountability Act (HIPAA) is like the Bible for patient data protection in the United States. It has strict privacy and security standards. Even for any kind of transfer of patient health information (PHI), you must adhere to the rules.
Key Provisions: HIPAA has set clear rules starting from how PHI can be used and disclosed, if applicable under any circumstances.
Say, for example, as a healthcare provider, you need to get written consent from your patients before sharing their data with any third party, even if it is another healthcare provider or an insurance company.
Even while transferring or sharing data in such instances, you must ensure it is encrypted.
Compliance Requirements: As healthcare providers, you must conduct risk assessments. A classic example of this would be to ensure that your firewalls are up-to-date.
You should also have strict administrative, physical, and technical policies in place. In any unfortunate case of a breach, you also should have procedures handy.
GDPR: Protecting EU Citizens’ Data Globally
The General Data Protection Regulation (GDPR) is the European Union’s comprehensive data protection law. However, even if your healthcare organization isn’t based in the EU, you must comply with GDPR if you process the data of EU citizens.
Key Provisions: This law grants extensive rights over personal data to individuals, including the right to access, rectify, and even erase it.
Compliance Requirements: Healthcare providers need to have individuals’ clear approval for data operation, designate a Data Protection Officer (DPO), and take relevant technical and administrative steps to secure information.
Beyond HIPAA and GDPR: Other Regulations
Several other regulations may apply depending on your location and the nature of your services. These include:
California Consumer Privacy Act (CCPA):
CCPA gives Californian residents the right to know what data is being collected, to delete their data, and to opt out of the sale of their data. (Yes, data being sold is a whole different topic!)
State-Specific Laws:
Many states have their own data privacy laws, which may be more stringent than federal regulations. So, it is wise to stay informed and keep yourself up-to-date about the laws applicable in your jurisdiction.
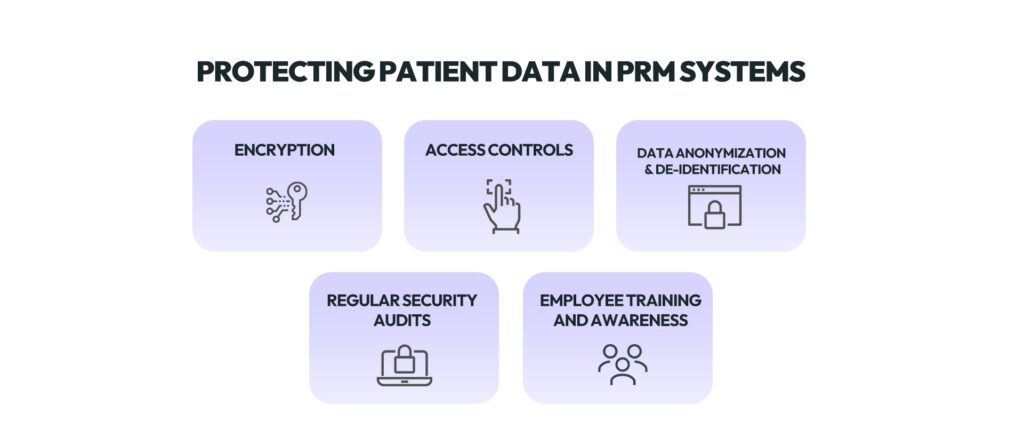
4. Strategies for Ensuring Patient Data Protection
Encryption:
Encryption makes the data unreadable to unauthorized individuals. It’s your strongest defense against data theft.
Types of encryption:
- End-to-end encryption: Protects data during transmission between devices, just like how your WhatsApp texts are. Nobody except the sender and receiver can decrypt the message, not even the service provider.
- Data-at-rest encryption: Secures data while stored on servers or devices. Even in case of a theft or data leak, if a hacker gains access to the storage, they can’t read the data without the encryption key.
- Database encryption: Encrypts entire databases, adding an extra layer of security to all the sensitive patient records.
- File-level encryption: Encrypts individual files or folders within a system, offering granular control over who can access specific data.
- Transparent data encryption (TDE): Automatically encrypts your data with little effort needed from users or administrators. This helps your information stay secure without a lot of manual work.
Access Controls:
Access controls ensure that only authorized personnel can view or modify patient information.
Best practices: Implement role-based access (different permissions for different roles) and multi-factor authentication (e.g., password + fingerprint) for maximum security.
Data Anonymization and De-identification:
Anonymizing or de-identifying patient data removes personally identifiable information (PII). This makes it safe for research and other secondary uses with zero compromise on privacy.
The most common methods include removing direct identifiers (names, addresses), masking indirect identifiers (dates, zip codes), and aggregating data.
Regular Security Audits:
Regular audits help you identify vulnerabilities in your PRM system before they’re exploited. You can consider hiring cybersecurity firms or using specialized software to assess your system’s security.
Employee Training and Awareness:
Even the most secure system can be compromised by human error. So, frequent training sessions should be conducted for your team so that they’re aware of security protocols. Roleplays can also help them be prepared and easily recognize potential threats.
Some topics to get started with can be – password hygiene, phishing scams, and recognizing suspicious activity.
5. Compliance with HIPAA and GDPR
HIPAA (US):
- Risk assessment: Go through your processes frequently and look for any vulnerabilities.
- Policies & procedures: Clear and written guidelines on handling PHI are a must. Once the rules are in place, onboard all of your team members.
- Breach notification: Have a plan in place before a breach occurs. This will help in mitigating damage.
GDPR (EU):
- Data Protection Officer (DPO): If you process large amounts of sensitive data or regularly monitor individuals, a DPO is mandatory. This expert ensures compliance and is your go-to person for data inquiries.
- Data subject rights: As granted by GDPR, EU citizens have the right to access, rectify, and erase their data. So, your systems must be ready to handle these requests.
- Data processing agreements: If you are working with any kind of third-party vendor, you must have a contract explaining their responsibilities clearly. This should include how they handle PHI and how they protect data. Don’t assume they have the same standards as you.

6. Best Practices for Safeguarding Patient Information
Implementing a Comprehensive Security Framework
- Frameworks and Standards: Be acquainted with gold-standard security frameworks like NIST or ISO 2700. This will provide a structured approach to managing risks and building robust security.
- Layered Security Approach: Think of security like layers of an onion. A single firewall isn’t enough. Implement multiple layers of defense, including encryption, access controls, detection systems, and regular vulnerability assessments. This makes it harder for attackers to penetrate through your system.
Ensuring Interoperability Without Compromising Security
- Secure Data Exchange: Interoperability is the ability of different systems to exchange data. This is unavoidable in healthcare. However, it can also bring in threats. So, use secure protocols like HTTPS for any kind of data transmission and have clear agreements with partners on data handling and security responsibilities.
- APIs: APIs (Application Programming Interfaces) are your gatekeepers. APIs control how data is accessed and shared between systems. Ensure your APIs are secure, well-documented, and regularly updated.
Monitoring and Incident Response
- Constant vigilance: Being on top of your PRM system allows you to detect suspicious activity early and respond promptly.
- Incident response plan: Having a clear-cut plan for handling security incidents before they happen goes a long way. This should include clear roles and responsibilities, communication protocols, and steps in case of a breach.
7. Conclusion
Throughout this blog, we’ve explored how critical data privacy and security in Patient Relationship Management (PRM) systems are.
By remaining vigilant and adaptable with us, ensure that your patient information remains confidential, secure, and out of any threat. Our mission is to help healthcare providers like you navigate these complexities while you focus on your core game – your practice!
Are you ready to revolutionize your practice? Schedule a demo today!
Together, we can elevate the patient experience and redefine the standard of excellence in dental practices nationwide.